
Ethical Hacking: White Hats Making The Digital World Secure
In today’s digital age, the term ‘Ethical Hacking’ is like a safety check. It is a crucial line of defense in our interconnected world. Simply put, ethical hacking is when hackers test computer systems to find and fix weak spots. This has a critical role because we hear about online fraud and phishing attacks all the time.
Ethical hacking is the good side of the hacking world. It’s about diving into systems, not to exploit, but to protect. It’s about wearing the white hat in a realm where not everyone plays by the rules.
Now, let’s break it down a bit. On one side, we have our heroes, the White Hats. These are the ethical hackers, the tech-savvy experts who use their skills to find and fix security gaps. They’re the digital guardians, ensuring our data stays safe and sound.
On the other side, there are the Black Hats. These are the experts with similar skills but different intentions. They’re out to find system loopholes, not to fix them, but to exploit them. It could be for money, fame, or just the thrill, their actions cause real damage.
But somewhere in between, we find the Grey Hats. These hackers might not always ask for permission but they do not necessarily have harmful intentions. They might spot a weakness, sneak in, but then give a heads-up to the organization about the gap they found.
Understanding these different hats is essential. It reminds us of the importance of ethical hacking and the role it plays in keeping our online world a safe place to work on.
The Ethical Framework: A Moral Compass
Ethical hacking, by its very name, carries a sense of responsibility. It’s not just about skills, but also about the ethics and principles that guide it. At its core, ethical hacking is about doing the right thing and ensuring that digital spaces are safe for everyone.
Consent is Everything. Ethical hackers don’t just dive into systems on impulse. They seek and have permission. They’re invited to test and explore, ensuring that systems are strong and secure. This separates them from malicious hackers who operate without any permission.
Boundaries are crucial too. Even with permission, there are limits. Ethical hackers respect them, ensuring they don’t overstep or cause unintended harm. They understand the importance of staying within the agreed-upon scope of their work and legalities can’t be ignored.
Ethical hacking might sound like a grey area, but it’s not. There are clear legal frameworks that define what’s acceptable and what’s not. Stepping outside these can lead to serious repercussions.
Ethical hackers work with integrity and report vulnerabilities. They respect client confidentiality and they do not misuse their access. They do not disclose vulnerabilities publicly without consent. And they certainly do not harm the system they’re testing.
The world of ethical hacking is guided by a strong moral compass. It’s a domain where skills meet responsibility, ensuring the digital world remains a safe space for all.
The Ethical Hack: A Step-by-Step Guide
An Ethical Hack is like a detective starting an investigation in a systematic and methodical manner. Let’s follow through this process.
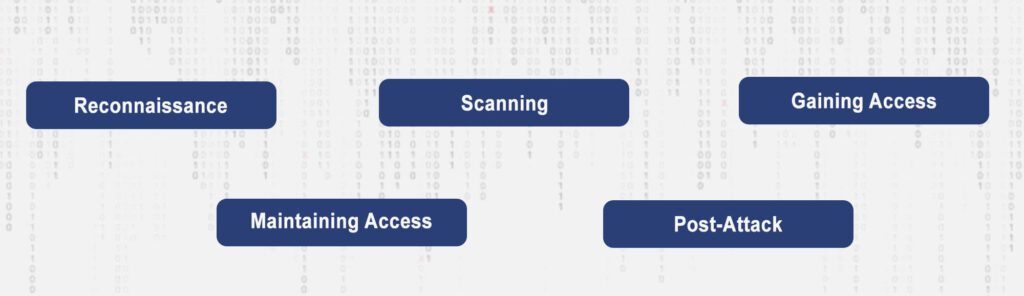
- Reconnaissance: This is the initial phase, often linked to a burglar stalking out a house before a heist. Ethical hackers gather as much information as possible about the target system. They look for domain names or IP addresses linked to a company in order to understand the target, but from a distance.
- Scanning: Now, the hacker gets a bit closer. Think of it as the detective using a magnifying glass to find fingerprints. In this phase, ethical hackers identify open ports or services running on servers. Tools like Nmap or Nessus might be used here. They help in detecting potential vulnerabilities in the system.
- Gaining Access: This is the action phase. The hacker tries to exploit the vulnerabilities they’ve found. It’s like the detective finding an unlocked back door. They might use tools like Metasploit to find a way in. It is important to understand ethical hackers have permission and they are testing the locks and not stealing anything.
- Maintaining Access: Here, the hacker acts like a spy, trying to create a backdoor for themselves. It’s about seeing if they can remain undetected in the system, highlighting potential risks. Can they stay without the system’s knowledge? If yes, then there’s a problem.
- Post-Attack: Once the testing is done, ethical hackers must report their findings. It’s like a detective presenting evidence in court. They detail vulnerabilities found, data accessed, and how long they remained undetected. This information is crucial for strengthening the system further.
Tools and Techniques for Ethical Hacking
In the tech world, tools and techniques are essential. They are what make the process efficient and effective. Similarly, many are used in various stages of hacking.
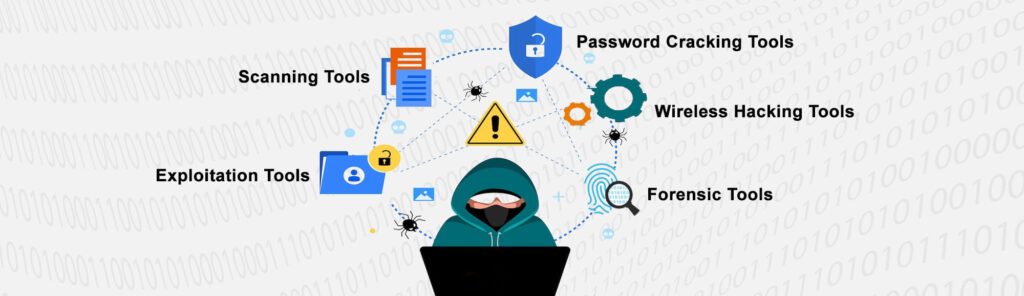
- Exploitation Tools: Metasploit is a big name here. It’s an application designed to find and exploit vulnerabilities. It’s like a locksmith’s set, helping hackers test every lock.
- Password Cracking Tools: Sometimes, hackers need to crack passwords. Tools like John the Ripper or Hydra come into play. They test the strength of passwords, ensuring they are robust enough to keep intruders out.
- Wireless Hacking Tools: In our wireless age, tools like Aircrack-ng are vital. They test the security of wireless networks. It’s about ensuring that Wi-Fi networks are as secure as their wired counterparts.
- Forensic Tools: Post-attack, tools like Wireshark help in analyzing what happened. They dissect the hack, helping organizations understand and learn from it.
Ethical Hacking is a thorough process. It’s about understanding, testing, and strengthening digital defenses. With the right tools and a systematic approach, ethical hackers ensure that the digital world remains a bit safer for all of us.
Why Ethical Hackers Are Essential

For some years, cyber threats are escalating at an alarming rate. From data breaches to ransomware attacks, the online world faces constant threats. Despite this chaos, ethical hackers emerge as heroes. They’re the first line of defence, proactively identifying vulnerabilities before malicious hackers can exploit them. Their role is not just about finding weak spots but also recommending robust solutions to fortify these digital fortresses.
Another instance is the “Heartbleed” vulnerability in OpenSSL. Ethical hackers were instrumental in identifying and mitigating this critical bug, preventing potential chaos.
The Learning Roadmap: Becoming an Ethical Hacker
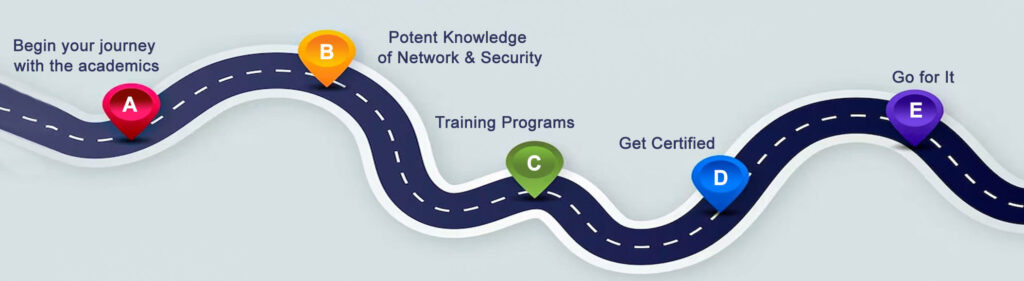
Thinking about becoming an ethical hacker is similar to setting out on an academic adventure. There is an oversupply of resources available for aspiring hackers. Platforms like Udemy, Coursera, and edX offer courses tailored for beginners and experts alike. For those seeking a structured learning path, certifications like CEH (Certified Ethical Hacker) or OSCP (Offensive Security Certified Professional) provide comprehensive curriculums.
Starting as a beginner, the world of hacking might seem overwhelming. But remember, every expert was once a beginner. The initial steps involve understanding basic cybersecurity concepts, networking, and operating systems and advanced steps include penetration testing, vulnerability assessment, and intrusion detection.
In the hacking community, certifications aren’t just pieces of paper; they’re badges of honour. The CEH certification equips learners with hands-on hacking techniques. GPEN (GIAC Penetration Tester) is another esteemed certification, focusing on penetration testing methodologies. For those seeking a challenge, OSCP is known for its rigorous 24-hour hacking exam. Lastly, CREST provides recognized accreditations in the penetration testing field. These certifications not only enhance knowledge but also open doors to lucrative career opportunities in cybersecurity.
In essence, becoming an ethical hacker is a journey of continuous learning. With the right resources, dedication, and certifications, one can master the art and science of ethical hacking, ensuring the digital world remains a safer place for all.
Is Ethical Hacking Legal?

Ethical hacking, despite its noble intentions, is imprinted on complex legal grounds. Different countries have differing laws regarding cybersecurity and hacking. In many regions, ethical hacking is legal, but with conditions.
The key lies in authorization. Ethical hackers must have explicit permission to probe and test systems. Without this consent, even well-intentioned hacking can be deemed illegal.
The distinction between ethical and unethical hacking is razor-thin yet critically important. Ethical hackers, often termed “white hats,” operate with permission, aiming to strengthen systems. Conversely, malicious hackers, the “black hats,” intrude without consent, often with harmful intentions. It’s essential to understand this difference, as crossing from ethical to unethical territory can lead to severe legal consequences.
The consequences of unauthorized hacking are significant. Legal penalties can range from hefty fines to imprisonment, depending on the severity of the breach and jurisdiction. Beyond legal consequences, hackers might face damage to their reputation and career prospects.
Organizations can also suffer immense financial and reputational losses if they employ hackers who overstep their boundaries.
While ethical hacking plays a pivotal role in bolstering cybersecurity, it’s crucial to operate within the legal framework. Understanding the complexities of what’s permissible and what’s not is crucial for anyone venturing into this domain.
Conclusion
Ethical hacking represents this spirit of responsible exploration. It’s not about breaching boundaries, but about ensuring those boundaries are robust enough to withstand threats. By supporting ethical hacking, we’re fostering a culture where curiosity meets responsibility, and innovation aligns with integrity.
The world of ethical hacking is dynamic, mirroring the ever-evolving world of technology. As new technologies emerge and cyber threats upgrade, the strategies and tools of ethical hackers will adapt. This constant evolution ensures that ethical hacking remains relevant, effective, and indispensable in the face of changing cyber landscapes.
In conclusion, it’s crucial for all digital citizens, whether they be individuals, organizations, or nations, that they should embrace and promote ethical digital practices.
Ethical hacking is not just a profession; it’s a philosophy and a commitment to making the digital world safer for everyone.

